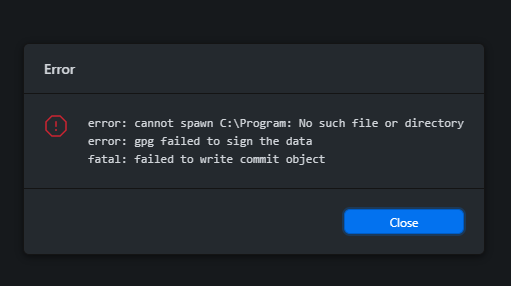
This blog post addresses the common issue of error: gpg failed to sign the data, helping readers understand the basics of GPG failures and their common causes. It provides a comprehensive guide on prerequisites for resolving GPG signing issues, alongside step-by-step instructions to fix the error. The article also reviews key tools for addressing GPG signing errors and compares different GPG key management options. Real-life examples illustrate common GPG signing challenges, while practical tips are provided to prevent such issues in the future. The key takeaways summarize vital points on error resolution and outline the next steps to take after fixing signing errors. By addressing the error: gpg effectively, users can ensure smoother operations and secure data signing.
Understanding The Basics Of Error: Gpg Failures
The error: gpg failure often arises during data signing processes, where the GPG (GNU Privacy Guard) fails to sign the data effectively. This situation can disrupt workflows and cause frustration, particularly among developers and system administrators who rely on secure signing for their software components and communications. Understanding the basic principles behind this error can be the first step toward effective troubleshooting and resolution.
When GPG encounters a problem while trying to sign data, the error message may indicate several issues ranging from improperly configured keys to software bugs. The causes of these errors can vary widely, and identifying the root cause is essential for implementing the right fix. For instance, ensure that the private key is properly loaded and that you have adequate permissions to access it.
| Cause | Description | Possible Solution |
|---|---|---|
| Missing Key | The signing key may not be accessible or loaded. | Import or reload the GPG key. |
| Permissions Issue | Insufficient permissions may restrict access. | Check and adjust permissions on your key files. |
| Incorrect Configuration | GPG may not be set up correctly. | Review your GPG configuration files. |
| Expired Key | The signing key might be expired. | Renew or replace the key. |
To address the error: gpg failures effectively, one might consider the following troubleshooting steps:
- Verify the presence of the necessary GPG keys.
- Ensure the correct key is the default for signing.
- Check for expired keys and renew them as needed.
- Review environment variables related to GPG.
- Confirm software updates and recent changes that may have impacted GPG.
Ultimately, understanding the factors leading to the error: gpg failure can empower users to resolve these issues quickly. By being proactive and familiarizing themselves with the diagnostic process, users can minimize disruptions caused by GPG errors in their workflows. Following these basic insights into GPG failures will set the groundwork for deeper investigation and resolution strategies discussed in upcoming sections of this article.
Common Causes Of Gpg Signing Errors
When working with GnuPG (GPG), encountering the error: gpg failed to sign the data can be frustrating. Understanding the common causes behind this issue is essential for troubleshooting effectively. Various factors, including configuration issues and key problems, could lead to this error. Recognizing these potential pitfalls can help users resolve the issue swiftly and ensure secure data handling.
A primary reason for the error: gpg issue often relates to incorrect key configurations. If GPG cannot locate the designated key for signing, it will lead to failure. Users might also face situations where the key has expired or been revoked, preventing successful signing. Hence, maintaining an updated keyring is crucial for efficient operations.
Common Causes of GPG Signing Errors
| Cause | Description | Solution |
|---|---|---|
| Missing Key | No GPG key available for signing. | Generate a new key. |
| Expired Key | Your signing key has expired. | Renew your key. |
| Revoked Key | Key has been revoked, cannot sign. | Use a different key. |
| Configuration Error | Wrong setup in GPG configuration files. | Review GPG settings. |
Another common issue leading to the error: gpg failure is file permission problems. If the files involved in the signing process do not have the correct permissions set, GPG may deny access, leading to signing errors. Ensuring the user has full read/write permissions on the required files can prevent such issues from arising.
Key Factors to Check When Troubleshooting GPG Signing Errors:
- Verify that the signing key exists and is correctly configured.
- Ensure the key has not expired or been revoked.
- Confirm file permissions for the documents being signed.
- Check GPG configuration for errors.
- Inspect the GPG agent for issues.
- Update GPG to the latest version.
Lastly, user environment issues can also contribute to the error: gpg. Differences in operating systems or user profiles may affect how GPG executes commands. In some cases, environmental variables can unintentionally redirect processes or inhibit proper access to necessary resources. Therefore, a comprehensive review of the user environment can aid in identifying the root cause of the signing error.
Prerequisites For Resolving Gpg Signing Issues
Before tackling the error: gpg messages, it is essential to prepare adequately to streamline the resolution process. Having a robust understanding of your GPG setup and potential conflicts can pave the way for successful troubleshooting. Addressing these prerequisites can significantly reduce downtime and enhance your overall productivity.
One of the foundational steps in resolving error: gpg is ensuring that your GPG key is properly configured and active. This involves not only the verification of the key’s existence but also ensuring that it is the correct one being utilized for signing. Additionally, it’s important to check that your GPG version is up to date, as newer versions often fix bugs and enhance performance, ultimately helping to circumvent issues.
| Prerequisite | Description | Status |
|---|---|---|
| GPG Key Installed | Verify that a GPG key is generated and available. | ☑️ |
| Configuration Check | Ensure correct setup in .gnupg directory. | ☑️ |
| GPG Version | Update to the latest GPG version for optimal performance. | ☑️ |
Another key aspect is to ensure that other software tools interfacing with GPG are functioning correctly. Sometimes, integration issues can cause the error: gpg to surface. Properly configuring dependencies like Git or any other applications interacting with your GPG signing setup can alleviate signing problems and lead to a smoother workflow.
Steps To Prepare
- Verify that the GPG key is active and correctly configured.
- Check for updates to the GPG software installation.
- Review configurations in the GnuPG directory.
- Ensure any software invokes GPG correctly.
- Backup existing GPG keys before making changes.
- Consult official GPG documentation for additional insights.
By aligning these prerequisites effectively, you gear up your environment for a seamless address of error: gpg occurrences, thus enhancing your operational efficiency.
Step-By-Step Guide To Fix Error: Gpg
Encountering the error: gpg message can be frustrating, but with the right guidance, you can resolve it effectively. The issue often pertains to the inability of GPG to sign data, which can interrupt critical workflows. Before diving into the solutions, it’s essential to identify some of the underlying causes that lead to this problem.
In many cases, the error stems from a misconfiguration in your GPG setup or the absence of a key. It’s advisable to check that you have the correct permissions set for your GPG keyring. Additionally, ensure that the GPG agent is running. If these initial checks don’t yield resolution, it’s time to take a more hands-on approach to reconfigure your settings and fix the issue.
Common Causes of GPG Signing Errors
| Cause | Description | Fix |
|---|---|---|
| Missing GPG Key | Your key may not be loaded or could be expired. | Import or renew the key. |
| Incorrect Permissions | File or directory permissions may restrict access. | Adjust permissions accordingly. |
| GPG Agent Not Running | The GPG agent might not be initiated, blocking operations. | Start the GPG agent using the terminal. |
| Configuration Issues | Misconfigured GPG settings can lead to signing failures. | Check .gnupg directory configurations. |
Once you’ve identified some potential key issues, it’s time to put proactive measures into action. Here is a structured approach:
- Check GPG Key Availability: Verify that your GPG key is accessible and properly loaded.
- Verify Agent Status: Ensure the GPG agent is running smoothly to facilitate operations.
- Adjust File Permissions: Review and amend file permissions that may restrict access to GPG files.
- Renew or Re-import Keys: If your key is expired, renew it or re-import it to rectify the issue.
- Update GPG Configuration: Inspect and revise your configuration files to ensure they align with proper protocols.
- Use Diagnostic Commands: Utilize GPG’s debug options to gain insights into the error logs.
- Consult the Community: If problems persist, reach out to online forums or GPG documentation for additional support.
Identifying Key Issues
Understanding the specific reasons for the error: gpg is vital to effectively troubleshoot the problem. Common issues include a missing or expired GPG key and incorrect agent settings. You want to ensure that your GPG environment is properly set, as even minor misconfigurations can lead to considerable hindrances.
Reconfiguring Your Gpg Setup
After pinpointing the issues, you must take steps to rectify them. This may involve reconfiguring your GPG settings, which can be daunting but is essential for restoring functionality. Regularly backing up your GPG keys and configuration settings can save you from future complications regarding error: gpg. By following these best practices, you’ll minimize disruption and keep your tasks on track.
Key Tools To Address Gpg Signing Errors
Resolving the error: gpg requires the use of various tools that can help streamline the debugging and rectification process. Understanding which tools can assist can significantly expedite the troubleshooting experience. Here, we will delve into essential tools that every user encountering this error should have in their toolkit.
Among the primary utilities to consider is Gpg4win, a comprehensive suite designed for Windows that allows users to manage their GPG keys intuitively. Its graphical user interface simplifies the key generation and management process, making it suitable for beginners and experienced users alike. Additionally, users can leverage Kleopatra, which comes as part of Gpg4win, to easily manage their encryption keys.
| Tool Name | Platform | Functionality |
|---|---|---|
| Gpg4win | Windows | Complete key management solution |
| Kleopatra | Windows | Graphical key manager for GPG |
| GPG Suite | MacOS | All-in-one solution for macOS |
| GnuPG | Cross-Platform | Open-source implementation of GPG |
Additionally, it is critical to utilize GnuPG (GNU Privacy Guard), which serves as the backend for generating and managing GPG keys. Being an open-source tool, it operates across multiple platforms (Windows, Mac, Linux), ensuring versatility. For users who are more comfortable with the command line, GnuPG offers powerful commands for detailed control over key management and usage.
Essential Tools
- Gpg4win – A Windows-based key management suite
- Kleopatra – A graphical key manager
- GPG Suite – Comprehensive solution for MacOS users
- GnuPG – The primary command-line utility
- Pinentry – Tool for secure PIN entry
- Sequoia PGP – Modern implementation of PGP
Lastly, don’t overlook Pinentry as another vital component. This tool provides a secure interface for entering passphrases, which is essential to avoid security flaws while managing sensitive data. Each of these tools plays a specific role in addressing the error: gpg and enhances the overall workflow in managing GPG keys, ensuring a smoother experience for users tackling signing errors.
Comparing Gpg Key Management Options
When encountering the error: gpg message, it often signals an issue with your GPG key management setup. Understanding the various options available for managing GPG keys can significantly enhance your ability to sign data effectively and overcome these errors. Different management strategies have their strengths and weaknesses, making it essential to choose the right one based on your specific needs and expertise.
Among the most popular GPG key management options are built-in command-line tools, third-party applications, and key management services. Each of these methods comes with its own set of advantages. For instance, command-line tools offer a direct approach, while third-party applications often provide additional user-friendly features. Key management services can centralize key handling, making it easier to manage multiple users within an organization.
Management Options
- Built-in command-line tools (e.g. gpg)
- Third-party GUI applications (e.g. Kleopatra, Gpg4win)
- Key management systems (e.g. HashiCorp Vault)
- Cloud-based GPG services (e.g. Keybase)
- Hardware security modules (HSM)
- OpenPGP-compatible clients
- Dedicated key servers for public keys
The choice between these options largely depends on your environment and the complexity of your requirements. For individual users, command-line tools may suffice, while organizations may benefit from more robust key management systems. It’s also crucial to evaluate the learning curve associated with each option, as some might require additional training or support to implement effectively.
| Management Option | Pros | Cons |
|---|---|---|
| Built-in Command-Line Tools | Direct control, versatile | Steep learning curve |
| Third-Party Applications | User-friendly, GUI features | Dependency on external software |
| Key Management Systems | Scalable, centralized control | Complex setup |
| Cloud-Based Services | Accessibility, ease of use | Security concerns with data in the cloud |
Ultimately, selecting the best GPG key management option is integral to resolving the error: gpg messages you may encounter. Each method has its own unique features that cater to different user preferences and security requirements. Emphasizing the importance of a well-maintained key management strategy can lead to smoother workflows and reduced signing errors, thereby increasing productivity and security in your data handling processes.
Real-Life Examples Of Gpg Signing Challenges
When tackling the error: gpg issue, understanding real-life examples can provide valuable insights into common challenges encountered. Users often report various cases where GPG signing operations fail, leading to confusion and frustration. Each of these instances sheds light on the importance of proper key management and configuration, demonstrating how seemingly minor oversights can lead to significant errors.
One prevalent example is users facing difficulties when attempting to sign commits in version control systems like Git. The error may stem from not having the correct GPG key associated with their identity or not having the key added to their configuration. This can often manifest in scenarios where the user has multiple GPG keys, leading to confusion about which key is being used. To illustrate this, consider the following factors:
| Scenario | Issue | Resolution |
|---|---|---|
| Signing commits | Incorrect GPG key used | Update user configuration |
| Email mismatch | GPG setup with wrong email | Ensure email aligns with the GPG key |
| Expired keys | Use of an expired GPG key | Renew or generate new keys |
Another common scenario involves dealing with GPG passphrase prompts during automated processes. CI/CD pipelines often fail to sign data due to the absence of an accessible GPG agent or missing passphrase management. Automating GPG signing requires careful handling of passphrases, and any oversight results in the error: gpg alerts. For those experiencing this issue, setting up a secure way to handle passphrase storage is crucial.
Case Studies
- User forgot to export their GPG key public part, leading to failed sign attempts.
- Incorrect assumptions about existing configurations resulted in GPG signing failures.
- Lack of understanding around the use of GPG agents caused frequent prompts.
- Expired signing keys led to trust failures in repositories.
- Misalignment between commit author emails and GPG keys hindered signing capabilities.
- CI/CD setups failing to handle secure passphrase storage resulted in GPG errors.
- Accounts with multiple email identities facing visibility issues with GPG signatures.
These examples highlight how the error: gpg can manifest in diverse situations, making it necessary for users to thoroughly review their GPG configurations. Proper key management and a comprehensive understanding of how GPG interacts with various applications will significantly reduce the occurrence of such issues, helping practitioners maintain secure and functional workflows.
Tips For Preventing Gpg Signing Issues
Dealing with error: gpg can be frustrating, especially when it interrupts your workflow. To mitigate potential signing issues, it’s crucial to adopt preventive measures that can keep your GPG environment stable. Implementing best practices not only reduces the likelihood of encountering signing errors but also enhances your overall cryptographic literacy.
Understanding the aspects that contribute to error: gpg can help in managing your keys more efficiently. Regular updates to your software, ensuring secure key storage, and educating yourself about GPG functionalities are just a few of the many proactive steps you can take. Moreover, keeping your public and private keys secured ensures that unauthorized users cannot compromise your system.
| Tip | Description | Benefit |
|---|---|---|
| Regularly Update GPG | Keep your GPG software up-to-date to avoid compatibility issues. | Improved security and functionality. |
| Secure Key Storage | Use a hardware security module (HSM) or secure password manager. | Prevents unauthorized access to your keys. |
| Backup Keys | Create copies of your keys in a secure location. | Ensures recovery in case of data loss. |
| Educate Yourself | Learn about best practices in key management. | Enhances your overall security awareness. |
In addition to structural adjustments, cultivating a routine around your GPG usage can lead to significant improvements in preventing error: gpg occurrences. Below are some key informative strategies to incorporate:
Proactive Tips
- Regularly audit your GPG keys and configurations.
- Ensure your keys are valid and not expired.
- Employ passphrases for private keys to add an extra layer of security.
- Make use of GPG’s revocation certificates for compromised keys.
- Test the signing functionality periodically to catch issues early.
- Monitor community forums for updates on known issues and best practices.
By following these preventive measures, you can significantly reduce the occurrences of error: gpg and maintain a smoother workflow in your encryption practices. Staying proactive in key management sets a solid foundation for successful cryptographic operations.
Key Takeaways On Error: Gpg Resolution
When dealing with the error: gpg issue, it’s essential to grasp the various underlying concepts that contribute to successful resolution. Understanding the potential causes and solutions can significantly enhance the effectiveness of your GPG operations. This summary aids users in navigating the complexities associated with GPG errors.
To effectively address the error: gpg issue, it’s crucial to consider several actionable strategies. These strategies target common pitfalls, ensuring that you maintain a robust environment for GPG signing. Review the following table that summarizes the key approaches:
| Strategy | Description | Benefit |
|---|---|---|
| Key Management | Ensure proper handling of your GPG keys. | Reduces signing failures. |
| Environment Configuration | Check your software settings for GPG. | Increases compatibility. |
| Regular Updates | Keep GPG and related tools updated. | Avoids potential bugs. |
| Backup Keys | Always create backups of your GPG keys. | Prevents loss of access. |
Implementing the strategies above can alleviate many of the issues associated with the error: gpg. Equally, understanding the importance of maintaining updated and accessible key pairs contributes to a smoother signing experience. Regular audits of your GPG configuration can further assist in identifying areas for improvement.
Actionable Insights:
- Regularly verify your GPG key’s integrity.
- Utilize a passphrase to enhance key security.
- Audit your local GPG settings and configurations.
- Seek out community support for persistent issues.
- Document any changes made for future reference.
- Test signing in a controlled environment before deployment.
In summary, addressing the error: gpg not only requires a firm grasp of technical know-how but also an understanding of practical strategies and community resources. By implementing best practices and being proactive about managing your GPG workflow, you can significantly reduce the incidence of signing errors and streamline your cryptographic processes.
Next Steps After Fixing Gpg Signing Errors
Once you have resolved the error: gpg signing issues, there are several crucial steps to follow to ensure a smooth experience moving forward. It’s important not only to confirm that the immediate error has been rectified but also to implement practices that will help avoid similar challenges in the future. This proactive approach equips you with tools and knowledge that make GPG management more efficient.
To solidify your understanding, it is advisable to evaluate your system’s GPG configuration and keys. This can include checking for key expirations, ensuring that your keys are properly backed up, and double-checking your key server settings. Engaging in these tasks can enhance your security posture and reliability when signing data.
| Step | Action Required | Details |
|---|---|---|
| 1 | Validate Key Pair | Confirm that your public and private keys match and are intact. |
| 2 | Backup Keys | Create a secure backup of your GPG keys to prevent loss. |
| 3 | Update Configurations | Ensure all settings are current, especially for key servers. |
| 4 | Test Signatures | Perform test signatures to check for any lingering issues. |
Moreover, establishing a routine for managing your GPG keys can significantly reduce the chances of encountering the error: gpg in the future. Regularly scheduled checks and updates on your keys, configurations, and trusted contacts will keep your operations seamless. This ongoing vigilance is key to a secure experience with GPG.
Immediate Actions
- Validate your current GPG key pair.
- Backup existing keys securely.
- Check for any updates to your GPG software.
- Review your trust levels for contacts and key owners.
- Adjust your GPG configuration as necessary.
- Run tests to confirm functionality.
- Document your steps and changes made.
Following these steps creates a structural foundation for you to effectively manage GPG signing. Emphasizing these practices will not only reinforce your current solutions but also equip you with the necessary skills to handle any future error: gpg situations swiftly and effectively.
Frequently Asked Questions
What does the error ‘gpg failed to sign the data’ mean?
The error indicates that GPG was unable to sign a piece of data, often due to issues with the encryption key, configuration, or software environment.
What are some common causes of GPG signing errors?
Common causes include missing or expired GPG keys, incorrect permissions on key files, software conflicts, or issues with the GPG agent.
What prerequisites should I check before resolving GPG signing issues?
Ensure that you have the correct GPG keys installed, that they are properly configured, and that your GPG software is up-to-date.
What is a step-by-step approach to fix the error: gpg?
1. Verify the existence and validity of your GPG keys. 2. Check the GPG agent status. 3. Ensure proper file permissions. 4. Reconfigure the GPG environment if necessary. 5. Attempt to sign the data again.
What key tools can assist in addressing GPG signing errors?
Tools such as GPG debugging options, GPG key management utilities, and command-line interfaces can help identify and resolve signing errors.
How do different GPG key management options compare?
Options vary in usability, security features, and integration capabilities; some tools are designed for individual users, while others cater to enterprise environments.
Can you provide real-life examples of challenges faced during GPG signing?
Users often encounter issues such as key passphrase prompts that fail, conflicts with other cryptographic software, or inability to locate the signing key required for specific operations.
What tips can help prevent GPG signing issues in the future?
Regularly update GPG and its dependencies, back up keys, monitor key expiration dates, and maintain proper access permissions to key files.